Featured
Table of Contents
- – How Does A Vpn Work? Advantages Of Using A Vpn
- – Openvpn: How Secure Virtual Private Networks R...
- – What Is Openvpn Protocol? - Nordlayer Learn
- – Dispelling Myths: Openvpn Is Obsolete
- – Openvpn With Tcp/udp - What's The Difference?
- – Openvpn(8): Secure Ip Tunnel Daemon - Linux ...
- – Guide To Vpn Protocols: Using Vpns Securely ...
- – Best Vpn Security Protocols - Vpn Protocols ...
How Does A Vpn Work? Advantages Of Using A Vpn
When you have set up the app on the gadgets, proceed to step 5. Now you simply need to import the certificates and secrets currently created in the steps above. To do this, merely follow these steps: Copy the ca. crt, customer. crt and client. essential files from steps 2 and 3 above to the config directory site of each customer gadget.
It is among the best procedures. If you opt for a third-party VPN service, it's recommended that you choose a service provider that offers it in order to enjoy a highly safe online experience without fear of hackers. We hope this guide addresses all questions about how Open, VPN works, how to set it up and when you should utilize it.
The very first thing to understand about Open, VPN is that it is a VPN protocol. A procedure is a set of rules that. It figures out how to secure and identify information packets passing across VPN connections. There are several protocol choices for VPN users, including L2TP, TLS/ SSL, and IPSec.
Openvpn: How Secure Virtual Private Networks Really Work
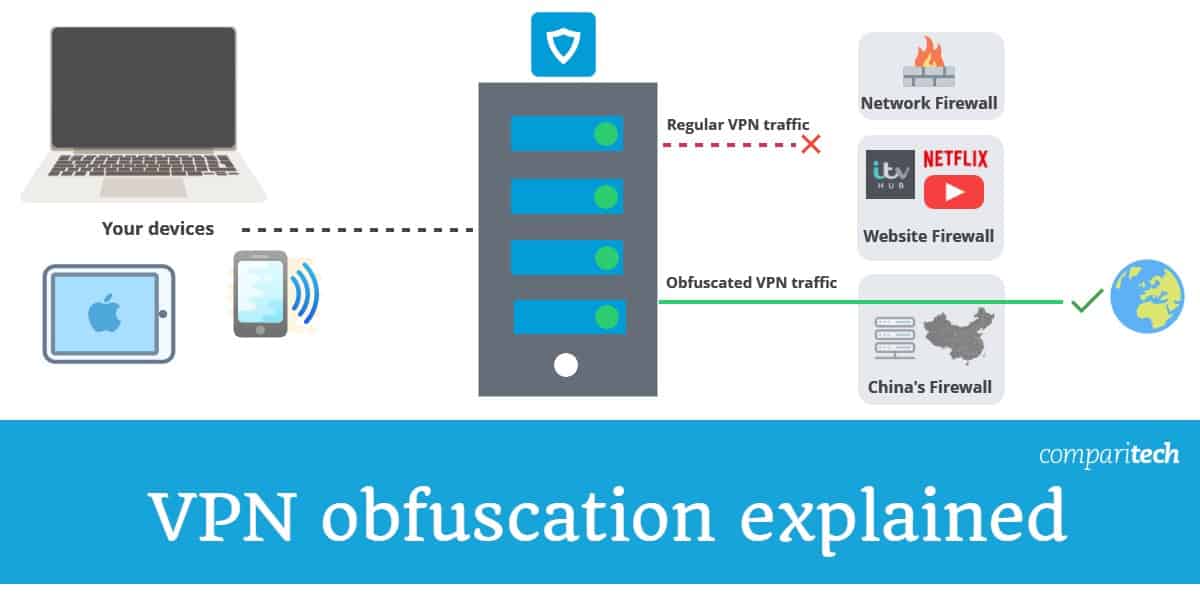
Open, VPN's open-source neighborhood checks bugs and fine-tunes the protocol, adding brand-new features and updating security aspects. Consistent scrutiny suggests that the procedure is.
Open, VPN systems can serve a single workstation linking to a company network or scale up to enterprise-wide security systems. One of the most significant Open, VPN advantages is that users can set up Open, VPN clients on Windows, Linux, and mac, OS.
Users will not need to trust that corporations protect information and prevent security mistakes. A worldwide coding community tweaks Open, VPN to respond to the current cybersecurity trends. The benefits listed above different Open, VPN from many other VPN procedures. No cybersecurity technology is perfect. Open, VPN is no exception, and there are numerous potential weak points users require to understand about:.
What Is Openvpn Protocol? - Nordlayer Learn
This is hassle-free, however business with bespoke security requirements might discover other procedures more user-friendly. Open, VPN has become a streamlined option for desktop and laptop os however is not as slick for mobile users. Android and i, OS applications are not as advanced or user-friendly, although they are enhancing all the time.
Transmission Control Protocol (TCP) is the other Open, VPN mode. In this case, TCP is categorized as a stateful protocol.
You might think Open, VPN is a type of VPN. Well. It's not. So, what is Open, VPN? How does it work? And why should you even care? We have all the responses. A VPN is a tool that lets you browse the web with some degree of privacy. It encrypts your web traffic information and paths it to a remote server, altering your IP address in the process.
Dispelling Myths: Openvpn Is Obsolete
Point-to-Point Tunneling Procedure is a prime example. The most popular ones are extremely configurable for a range of uses - you can make them as safe and secure and lightweight as the need arises.
It used to support Open, VPN and IPSec (Web Procedure Security), however Anchor, Free Inc. (its developer) felt both procedures had inappropriate latency issues. Over time, brand-new tunneling protocols come along to take it up a notch.
The Open, VPN protocol can be a pain to set up by hand. TCP and UDP Open, VPN procedures are normally preconfigured in a lot of VPN apps for individual use.
Openvpn With Tcp/udp - What's The Difference?
Other than Hotspot Shield, Hola VPN was the only other vendor we have actually experienced that didn't utilize Open, VPN. Still, a few of the most popular VPN services - like PIA, Surfshark, Nord, VPN, and Express, VPN - support it. Open, VPN is one of the finest all-around VPN procedures out there.
Without a doubt, Open, VPN innovations are safe. It's no longer the best at many things with the advent of Wire, Guard.
Over the previous few years, Virtual Private Networks (VPNs) have become an incredibly popular method for securing yourself while using the internet. There's a series of VPN providers out there, such as Nord, VPN, Surf, Shark, and Express, VPN, however you may not have found out about the innovation they use.
Openvpn(8): Secure Ip Tunnel Daemon - Linux Man Page
What precisely is it? And how can you use it to encrypt your data? Open, VPN is an open source connection procedure that uses encryption and authentication to produce a protected "tunnel" in between the user and the server. You may have heard popular VPN providers use this sort of analogy when explaining their service, and that's because a lot of them utilize Open, VPN to supply you with online security.
This is one of the Open, VPN's key security elements, and stands as one of the most safe encryption methods out there today. On top of all this, Open, VPN is open source, meaning that anybody can see the code, and that any bugs can be determined and repaired rapidly by the Open, VPN neighborhood if the developers do not see to it initially.
How do you really use it? At this point, you may be believing, "if Open, VPN is so great, why haven't I heard of it prior to?".
Guide To Vpn Protocols: Using Vpns Securely In 2023
What numerous don't know is that Open, VPN, unlike the other suppliers mentioned above, is absolutely free to use, suggesting you'll never ever have to deal with any in advance charges or membership fees. Can Open, VPN be utilized as quickly as popular companies simply on its own?
This is another VPN procedure that can offer a more trustworthy connection and has a more protected kind of encryption. But only time will inform whether this protocol becomes the next big thing in online security. While it's simple to register for a subscription-based VPN service with simply a couple of clicks of the mouse, you might wish to consider giving Open, VPN a go if you desire the very same innovation without an in advance or regular monthly cost.
To have the Open, VPN protocol described, we 'd say it's the most flexible of them all. It's an open-source solution, implying that anybody can access it and modify its code. There are 2 primary options when it concerns Open, VPN. Open, VPN Community Edition is the standard, free variation of the software, while Open, VPN Gain Access To Server is the sophisticated, paid version.
Best Vpn Security Protocols - Vpn Protocols - Openvpn
Among the strengths of Open, VPN is that it can be used on both User Datagram Procedure (UDP) and Transmission Control Procedure (TCP). These are the communication requirements that enable devices to exchange messages over the network. From what we have experienced, Open, VPN with TCP is more trustworthy, while Open, VPN with UDP appears to be quicker.
Open, VPN is among the best VPN procedures on the marketplace. The main reason for that is that it's an open-source option, and no company owns or operates it. You can be entirely sure your data is safely transferred, and no one can get unapproved access to it or sell it to a third celebration.
Table of Contents
- – How Does A Vpn Work? Advantages Of Using A Vpn
- – Openvpn: How Secure Virtual Private Networks R...
- – What Is Openvpn Protocol? - Nordlayer Learn
- – Dispelling Myths: Openvpn Is Obsolete
- – Openvpn With Tcp/udp - What's The Difference?
- – Openvpn(8): Secure Ip Tunnel Daemon - Linux ...
- – Guide To Vpn Protocols: Using Vpns Securely ...
- – Best Vpn Security Protocols - Vpn Protocols ...
Latest Posts
Best Vpns For Business In 2023
The Top 10 Enterprise Vpn Solutions
7 Best Vpns For Mobile Phones - Expert Picks For 2023
More
Latest Posts
Best Vpns For Business In 2023
The Top 10 Enterprise Vpn Solutions
7 Best Vpns For Mobile Phones - Expert Picks For 2023